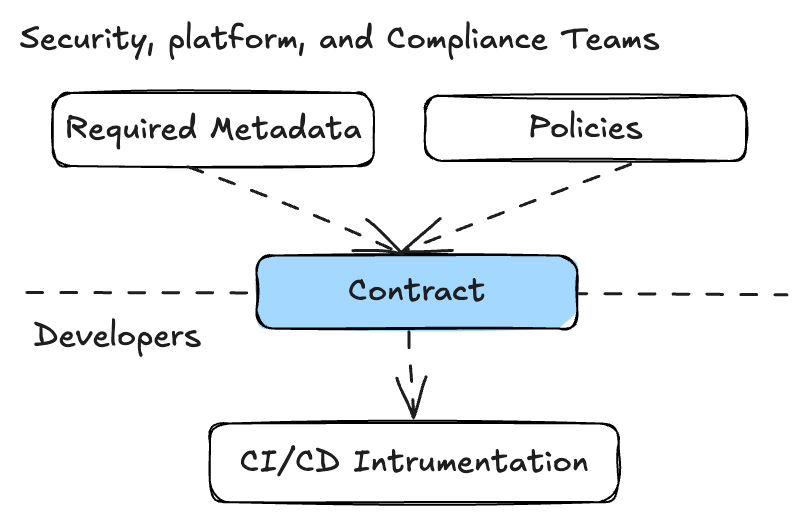
- A Workflow Contract is immutable and versioned, new revisions of the contract with new/different requirements can be added over time. This is especially useful for iterative integrations.
- A Workflow Contract can belong to more than one Workflow. This means that a change in a single contract will be propagated to many workflows. This is especially useful for org-wide standardization and fleet management.
Managing Contracts
- Web UI
- CLI
Contracts can be managed through the “Contracts” section in Chainloop platform:

- Web UI
- CLI
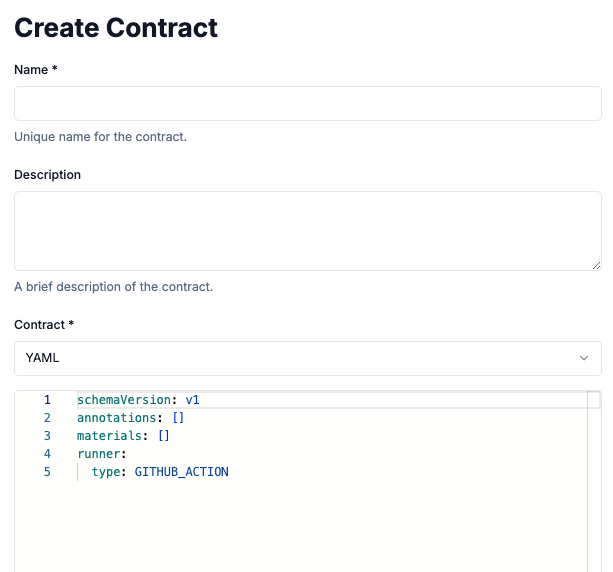
A Workflow Contract can be provided in json or yaml (cue format is also supported through the Chainloop CLI).
Contract Management Scope
Contracts in Chainloop operate at two different scopes with corresponding management permissions:- Organization-scope contracts: Managed by users with Organization Admin or Organization Owner roles. These contracts can be used across all projects within the organization.
- Project-scope contracts: Managed by Project Admins. These contracts are specific to individual projects and can only be used within their respective project scope.
Restricting Contract Creation
Organizations can optionally enable the “Restrict Contract Creation to Organization Admins” setting to enforce stricter governance over contract management. When this setting is enabled:- Only users with Organization Admin or Organization Owner roles can create new contracts (regardless of the contract scope)
- Project Admins that are not Organization Admins can no longer create their own contracts
- Workflows created by non administrators must use existing contracts
Enabling the setting
Organization owner and admins can enable this setting in the organization settings.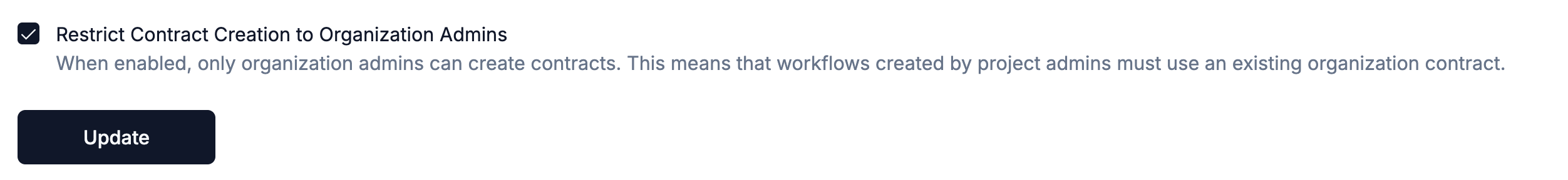
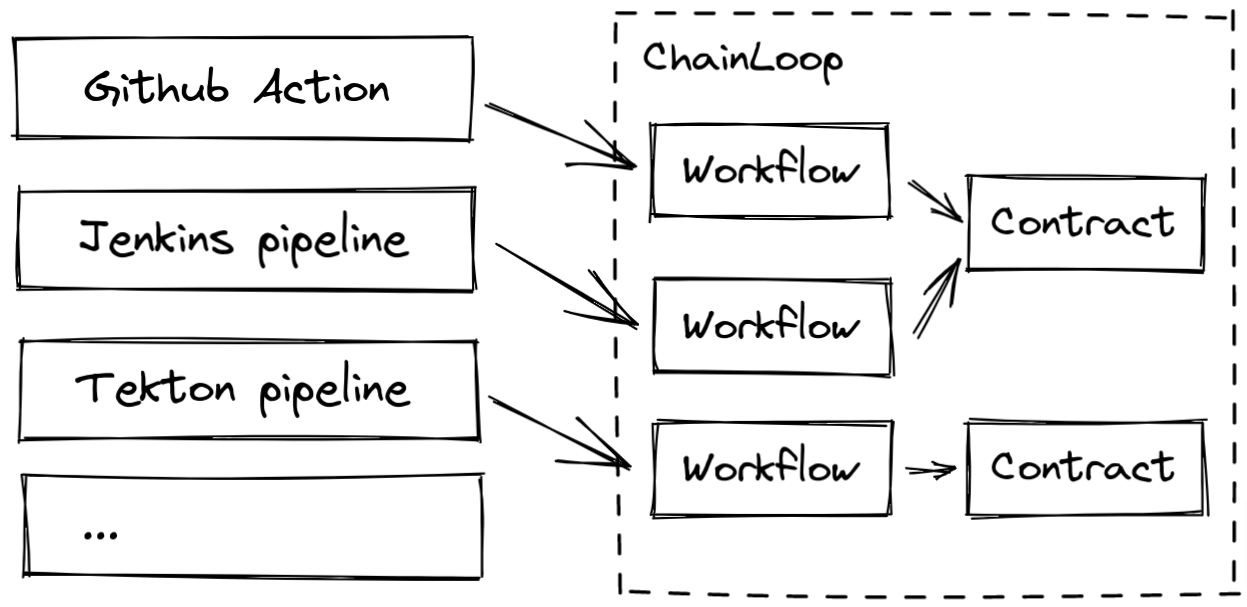
Associating workflows to contracts
Once contracts are created, they can be attached to as many workflows as needed. Remember that workflows represent a unique source of data ingestion (attestations), usually representing a CI/CD pipeline.- Web UI
- CLI
In the workflow view, click on the edit icon and associate the contract. Once the contract is associated, new attestations will automatically download and apply it, including required materials, policies, and so on.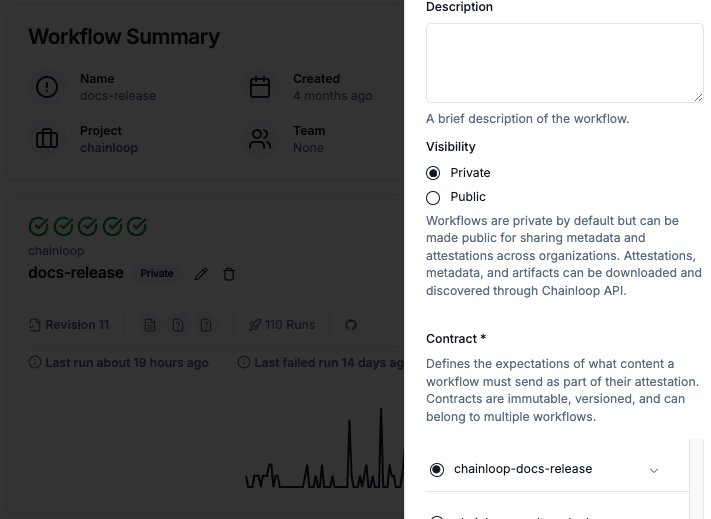

Writing contracts
Example
See below a contract schema example:Note that the contract below is just an example crafted for educational purposes. In a real scenario, the contract will not contain such a despaired amount of materials or annotations.
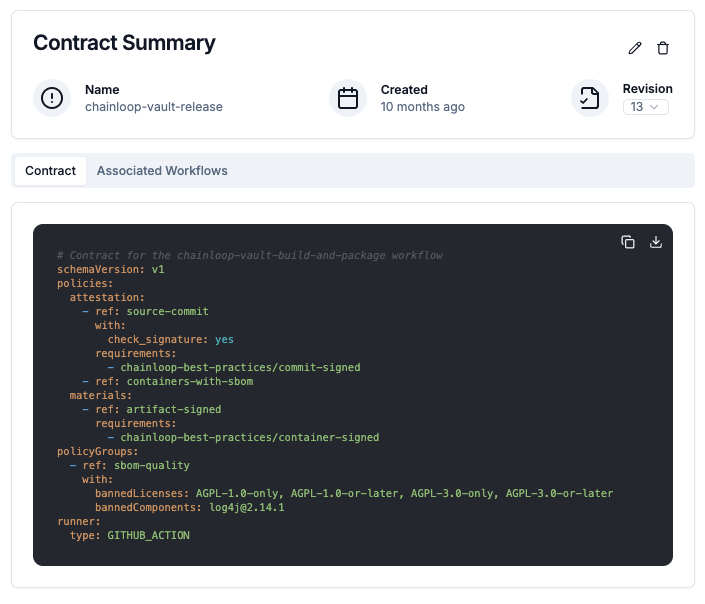
Schema
- Schema
- Deprecated Schema
| Name | Required | Description |
|---|---|---|
apiVersion | yes | API version of the schema, must be chainloop.dev/v1 |
kind | yes | Resource type, must be Contract |
metadata | yes | Metadata about the contract |
metadata.name | yes | Name of the contract |
metadata.description | no | Optional description of the contract |
metadata.annotations | no | Name/Value pairs of arbitrary annotations that will be added to the attestation. If the value is not provided, it will be required during the attestation process. |
spec | yes | Contract specification containing all contract configuration |
spec.materials | no | List of materials to be added to the attestation |
spec.envAllowList | no | List of environment variables that will be resolved and injected in the attestation |
spec.runner | no | Specific runner type associated with this contract. If not set, this contract will be valid to be run anywhere but you’ll miss out some of its benefits |
spec.policies | no | Attachments to existing Chainloop policies. See policies reference guide for more information |
Materials
The contract can require one or more pieces of evidence (a.k.a material) to be attached during the attestation process.| Name | Required | Default | Description |
|---|---|---|---|
name | yes | unique identifier of the material | |
type | yes | Refer to material-types for the list of supported material types. | |
output | no | false | If set to true the material will get injected in the subject section of the in-toto statement. |
optional | no | false | if set to true, providing this material during attestation will be optional. This is useful for soft rollouts of new requirements |
skip_upload | no | false | if set to true, the material will not be uploaded to CAS (Content Addressable Storage). Only metadata like digest and filename will be recorded in the attestation. This is useful for large artifacts already stored externally or when you want to reduce storage costs while maintaining attestation metadata. Note: CONTAINER_IMAGE and STRING types are not uploaded to CAS by default. |
annotations | no | Name/Value pairs of arbitrary annotations that will be added to the attestation. If the value is not provided, it will be required during the attestation process. |
Policy attachments
When defining a contract, a newpolicies section can be specified. Policies can be applied to any material, but also to the attestation statement as a whole.
Runner Context
New runner contexts will be added over time. If yours is not implemented yet, please contact us
skynet.contract.yaml showLineNumbers
- Require the attestation process to be executed in the target runner type unless the
--dry-runflag is set during initialization. - A link to the workload (i.e Github Action Run link) will be recorded both in the attestation and in the control plane during initialization.
- An additional set of environment variables will be resolved in addition to the ones defined in the contract
envAllowList.
AZURE_PIPELINE
The following environment variables will be automatically added to the attestation. For more information on what they mean, refer to this link.
BUILD_REQUESTEDFOREMAILBUILD_REQUESTEDFORBUILD_REPOSITORY_URIBUILD_REPOSITORY_NAMEBUILD_BUILDIDBUILD_BUILDNUMBERBUILD_BUILDURIBUILD_REASONAGENT_VERSIONTF_BUILD
CIRCLECI_BUILD
The following environment variables will be automatically added to the attestation. For more information on their meaning, refer to the official CircleCI documentation.
CIRCLE_BUILD_URLCIRCLE_JOBCIRCLE_BRANCH(optional)CIRCLE_NODE_TOTALCIRCLE_NODE_INDEX
DAGGER_PIPELINE
To use Chainloop With Dagger you can use this Dagger module
GITHUB_ACTION
The following environment variables will be automatically added to the attestation. For more information on what they do refer to this link.
GITHUB_ACTORGITHUB_REFGITHUB_REPOSITORYGITHUB_REPOSITORY_OWNERGITHUB_RUN_IDGITHUB_SHARUNNER_NAMERUNNER_OS
GITLAB_PIPELINE
The following environment variables will be automatically added to the attestation. More information about what they mean in GitLab’s official documentation
GITLAB_USER_EMAILGITLAB_USER_LOGINCI_PROJECT_URLCI_COMMIT_SHACI_JOB_URLCI_PIPELINE_URLCI_RUNNER_VERSIONCI_RUNNER_DESCRIPTIONCI_COMMIT_REF_NAME
JENKINS_JOB
The following environment variables will be automatically added to the attestation. For more information on how to use Jenkins environment variables, refer to the official Jenkins documentation.
JOB_NAMEBUILD_URLGIT_BRANCH(optional)GIT_COMMIT(optional)AGENT_WORKDIRNODE_NAME
TEAMCITY_PIPELINE
The following environment variables will be automatically added to the attestation. For more information on TeamCity environment variables, refer to the official TeamCity documentation.
BUILD_URLTEAMCITY_PROJECT_NAMETEAMCITY_VERSIONBUILD_NUMBERUSERTEAMCITY_GIT_VERSIONBUILD_VCS_NUMBERHOME
Gather Additional Runner Configuration
The Chainloop CLI Enterprise Edition provides a runner context that can be used to gather the runner context. When Chainloop CLI Enterprise Edition is used it enables automatic retrieval of the following data:- Branch protection rules
- Pull request requirements
- Commit policies
- Verifying that proper protections were in place during the build process
- Understanding what security measures are protecting the code
- Proving that security policies were followed during development

