This feature is only available on Chainloop’s platform paid plans.
Overview
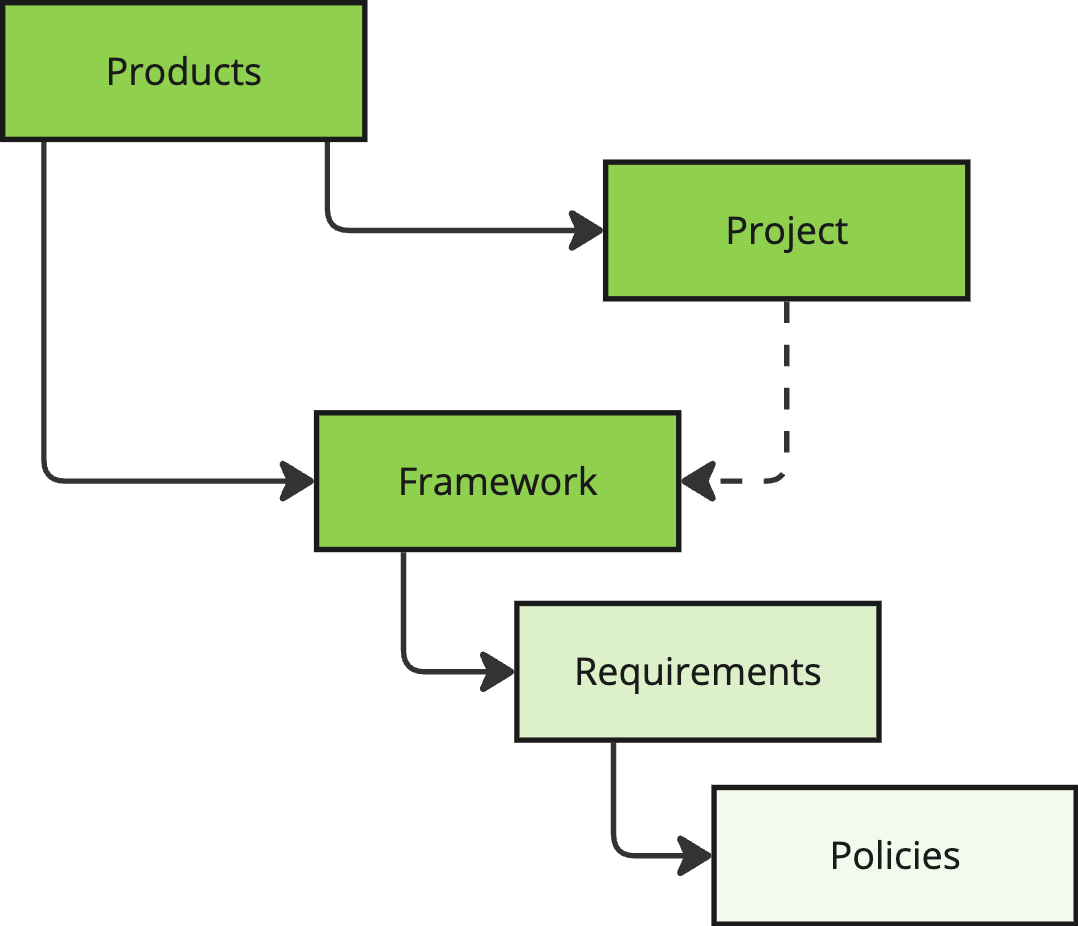
Compliance, Risk Management, and Release Management teams need a seamless way to communicate SDLC security and compliance requirements to development teams. This is critical in organizations with hundreds or thousands of different products. Chainloop provides a convenient way to model Projects (software products) and Versions. Then, Compliance teams can apply Compliance Requirements through Frameworks to these projects. Requirements can be written in a high-level language, like “container images must be signed”, “an AGPL license is forbidden”, “the software must be free from high-severity vulnerabilities”, “code repositories must be configured with least privilege principle access controls”, etc.
- Built-in: Chainloop provides a good set of pre-built frameworks and requirements that can be directly applied to projects or used as the basis for building custom. Built-in requirements can be used in custom frameworks or copied to custom requirements.
- Custom: Organizations can manage their own private org-level frameworks and requirements.
Supported Built-in Frameworks
| Framework | Type | Purpose | Coverage | Verification | Chainloop Docs |
|---|---|---|---|---|---|
| Best Practices by Chainloop | Custom policy set | Recommended internal basic security policies | Full tracking | Automated policies | |
| Cyber Resilience Act (CRA) | Regulation | Minimising risks on released software | In-preview | Self-assessment checklist, manual evidence, automated policies | Reference User Guide |
| SLSA | Specification | Securing the software supply chain | Full tracking | Manual evidence, automated policies | Reference User Guide |
| SSDF | Framework | Integrating security practices into software development lifecycle | In-preview | Self-assessment checklist, manual evidence, automated policies | Reference User Guide |
In-Preview Compliance Frameworks
By default, compliance frameworks are enabled in the Chainloop Platform. However, frameworks under active development and subject to change are available in-preview mode. These are disabled by default and require manual activation. To enable frameworks in preview mode, a team member with the role Owner or Admin can go to Settings → General, mark “Enabled” in the In-Preview Compliance Frameworks section and “Update”.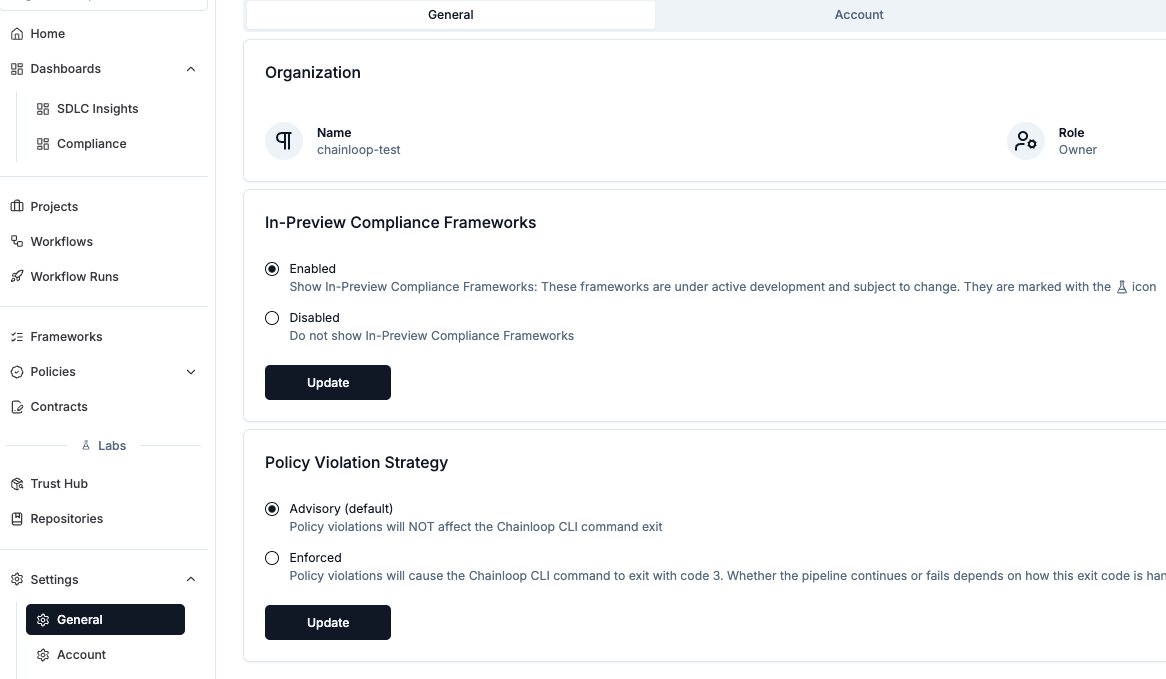
Using Frameworks
Using frameworks is a two steps process:- Connect an existing framework to a product
- Update your contracts to reference the requirements in the framework
1 - Attach Frameworks to Products
You can attach any existing compliance framework to any of your products by editing them from the product view.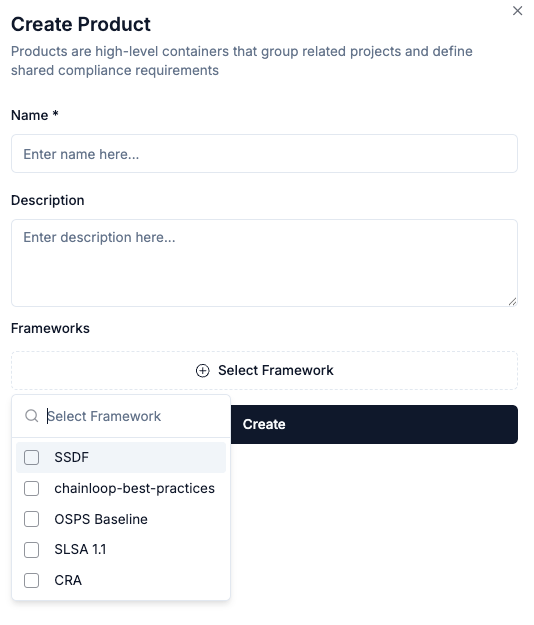
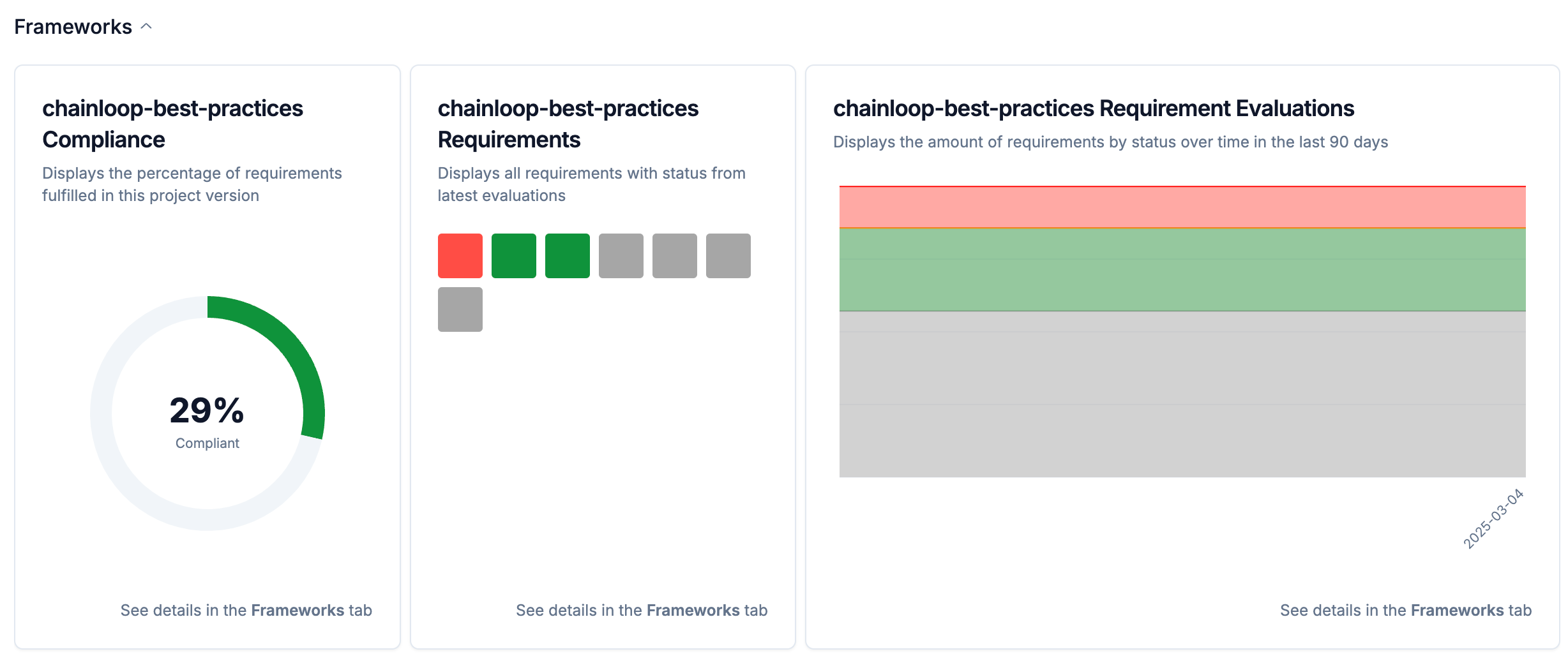
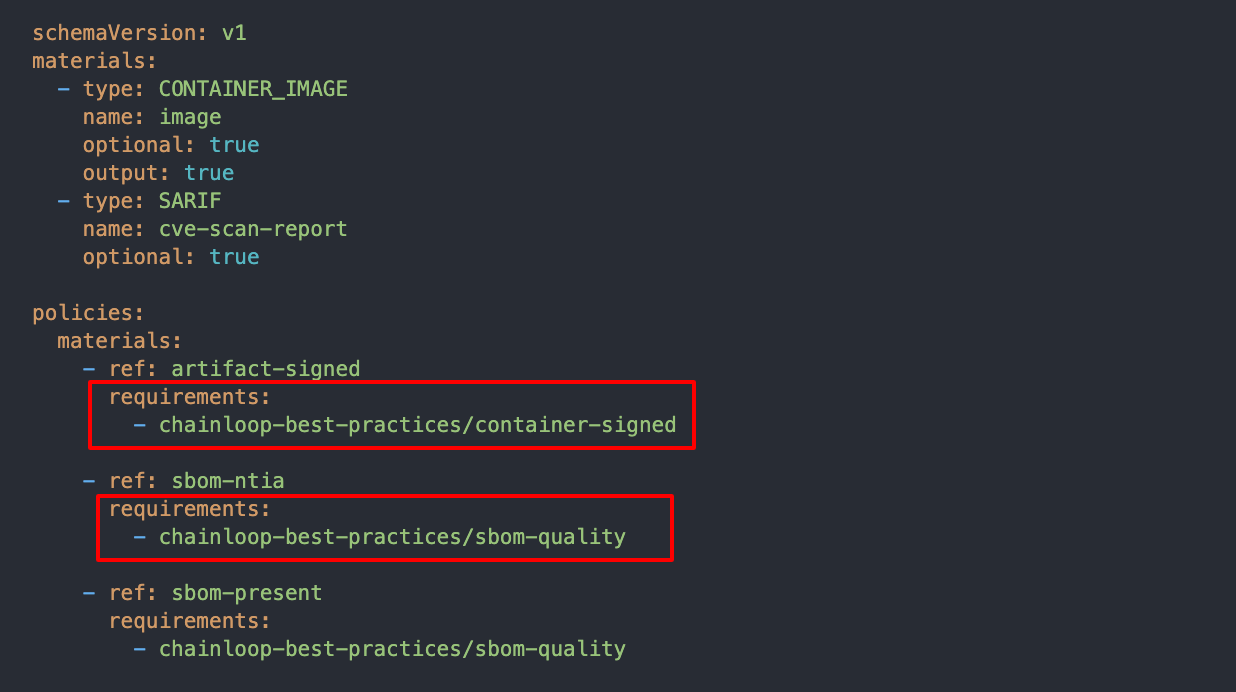
2 - Update Contracts to Reference Requirements
To comply with your project requirements, you need to attach policies to your contracts, adding the requirements list during its attachment in the form of[framework-name]/[requirement-name].
In the example below, we are attaching three policies and making them part of 2 requirements.
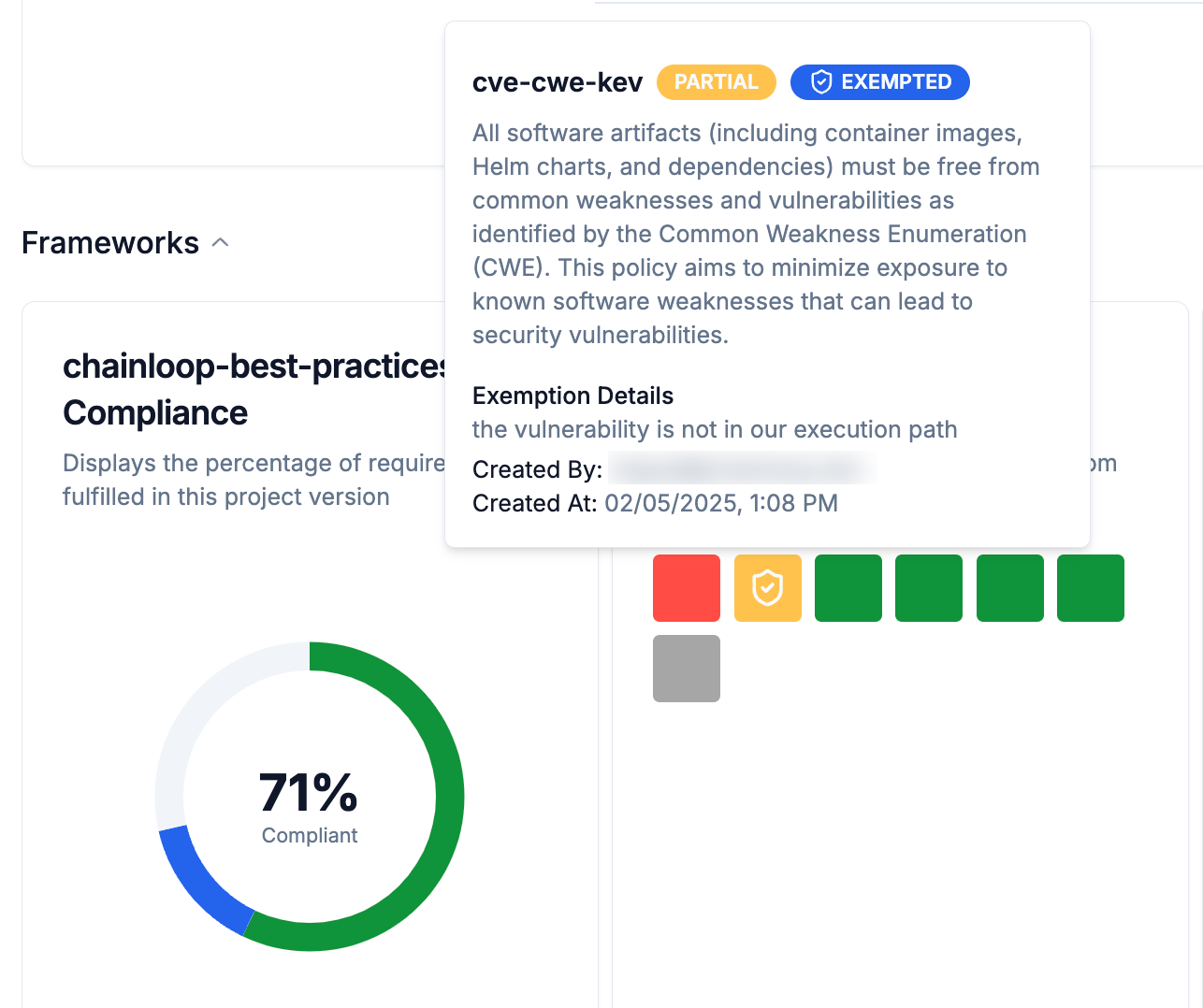
Record Requirement Exceptions
When you attach a compliance framework to a product, a set of expected requirements will be tracked over time for each related project, filling up your compliance and security posture. In some scenarios, not all requirements can be met before performing a release, so in that case, an “exception” can be added to a specific requirement.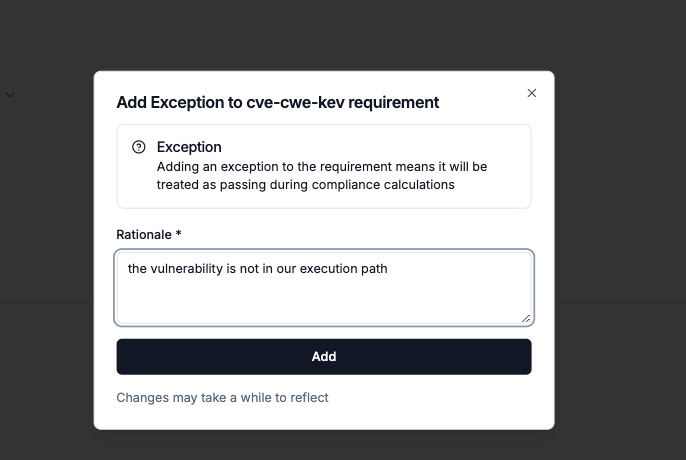
Requirement status overrides
In addition to exceptions, you can also manually override the status of a requirement to “Passed”, or “Failed”. This can be useful in scenarios where the automated evaluation does not capture the full context of the requirement compliance. The difference with exceptions is that overrides will be considered when calculating the final compliance status, while exceptions will ignore the requirement status.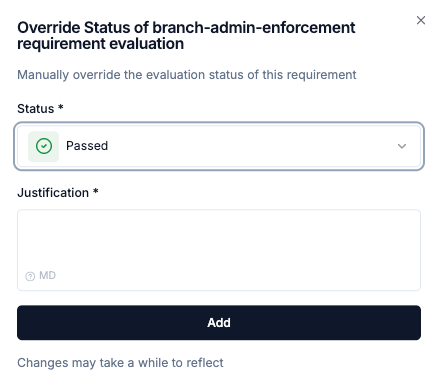
Custom frameworks or requirements
Apart from using the built-in frameworks and requirements, you can also create your own. You can either start from scratch or base your framework or requirement on an existing one by clicking on the duplicate icon.