This feature is only available on Chainloop’s platform paid plans.
- Configure your Chainloop Workflow to use the slsa-checks policy group and attach the SLSA framework to your project.
- Configure your CI workflow to generate OIDC tokens so we can do runner verification.
- Automatically verify SLSA compliance using Chainloop platform.
1 - Configure your Chainloop Workflow
We start by configuring Chainloop Workflow (full docs available here). We assume you already have chainloop command line tool available in your local environment (if you don’t have a look at the installation docs:CONTAINER_IMAGE representing our container image. We can add it during the build.
We also included the policyGroups section and referenced the slsa-checks that performs all the required checks for the SLSA framework.
2 - Configure your CI workflow to perform runner verification
The following section assumes you are using GitHub or GitLab as your build platform. More platforms are in the works, if you can’t see yours, please contact us.
GitHub Action
Addid_token write permission to your GitHub workflow file so Chainloop can verify that you are using a trusted runner.
GitLab Pipeline
If you are already performing keyless attestations, you can skip this step.
GITLAB_OIDC or performing keyless attestations.
In either way, the .gitlab-ci.yml file could look like this:
3 - Verifying SLSA level in Chainloop
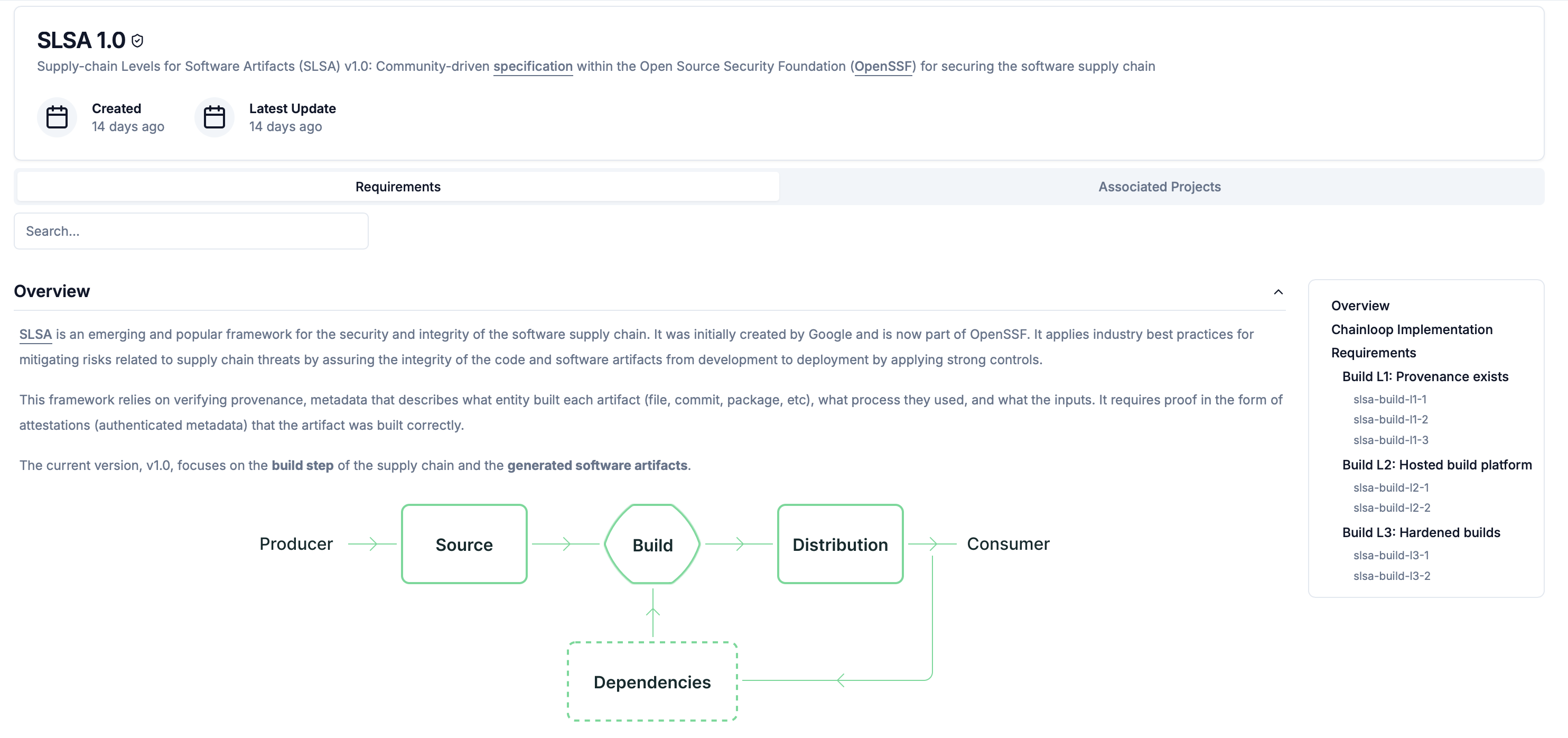
Now that we are already generating SLSA provenance and including it in the Chainloop attestation, we need to associate the SLSA Framework with the project we want to start monitoring SLSA compliance for. You can do that by going to the Project and selecting the project of you choice and updating it in the Update Project section of that page.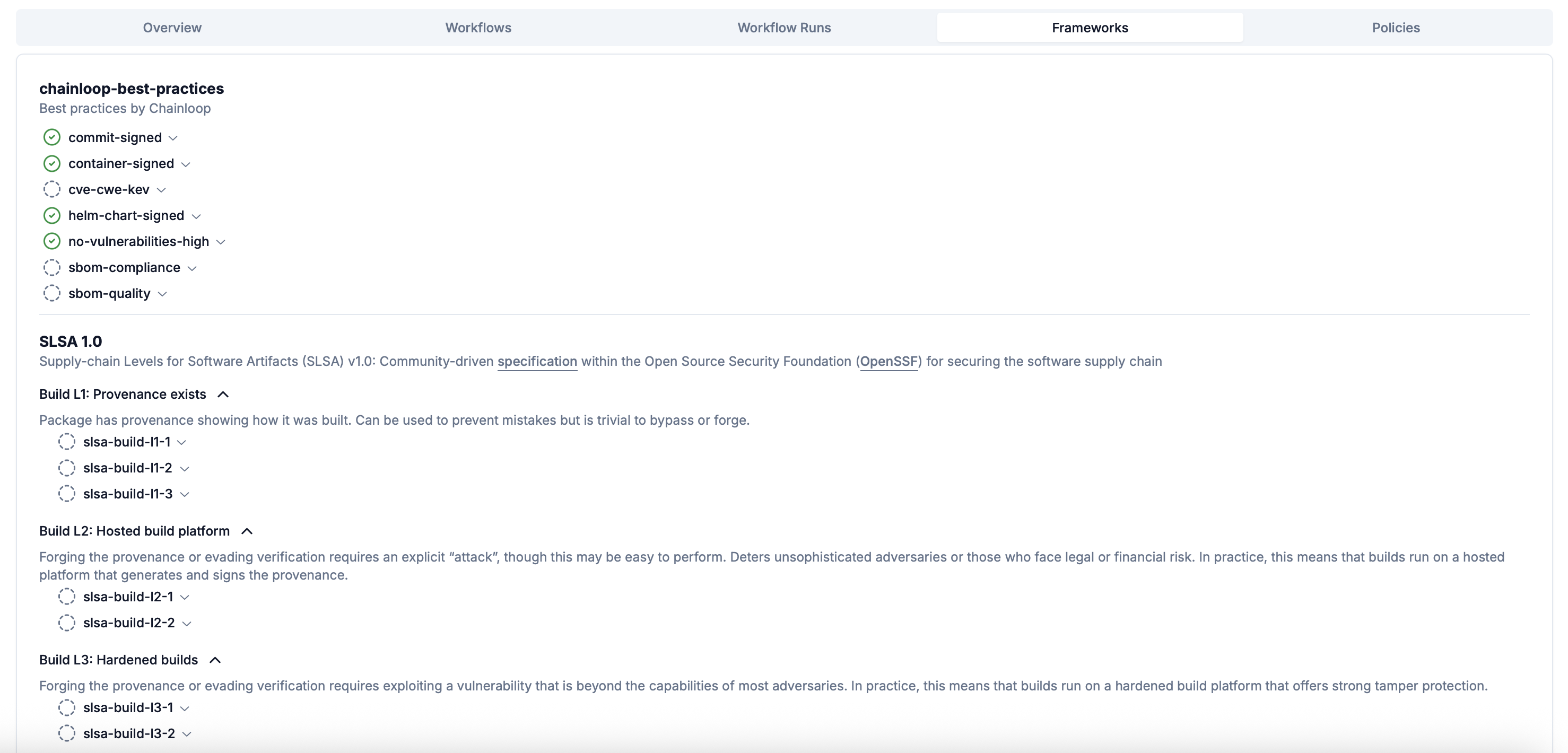
4 - Troubleshooting
When working with SLSA attestation you might run into the following errors:Runner not Authenticated
Chainloop will report that runner is not authenticated or that the workflow file path is missing when the OIDC token can’t be retrieved. The errors that you might see in your SLSA policies execution are:Runner is not authenticatedRunner workflow file path is missing or is empty
- GitHub
- GitLab
When using GitHub Actions, make sure that the
id_token permission is set on the workflow level, not job level. For example:Runner Environment is not Valid
Chainloop will report that runner environment is not valid when the runner environment is not as the one provided in the policy. This means that the build runner platform is not as expected. The expected and actual runner platform are provided in the error message. The errors that you might see in your SLSA policies execution are:Runner environment is not valid
Keyless Signatures not Supported
Chainloop will report that keyless signatures are not supported when the provenance is not signed. Verify that your build platform is using the newest version of Chainloop. The errors that you might see in your SLSA policies execution are:Keyless signing configuration is invalid or not found

