Attaching policies to the contract
- Web UI
- CLI
- Chainloop OSS
As we did before, let’s “Update our contract”, but this time the contract will contain policies and policy groups.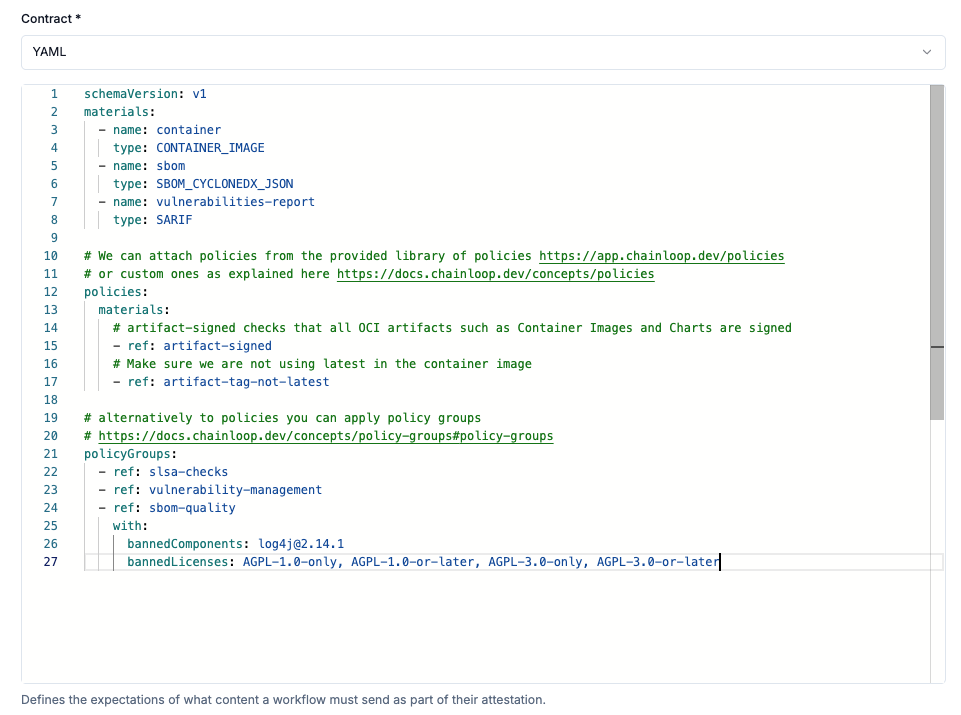

artifact-signedpolicy checks that all OCI artifacts (container images and Helm Charts) are properly signed with Cosign or Notaryartifact-tag-not-latestchecks that the container image is not using thelatesttagslsa-checksis a policy group that makes sure the attestation is compliant with the SLSA frameworkvulnerability-managementis a policy group that makes sure the attestation is compliant with the vulnerability management policysbom-qualityis a policy group that makes sure the attestation is compliant with the SBOM quality policy
Evaluating policies
Let’s create an attestation and add our materials to see how policies are evaluated:1
Initialize an attestation
2
Add the container image
3
Add the SBOM
4
Add the vulnerability report
5
Push the attestation
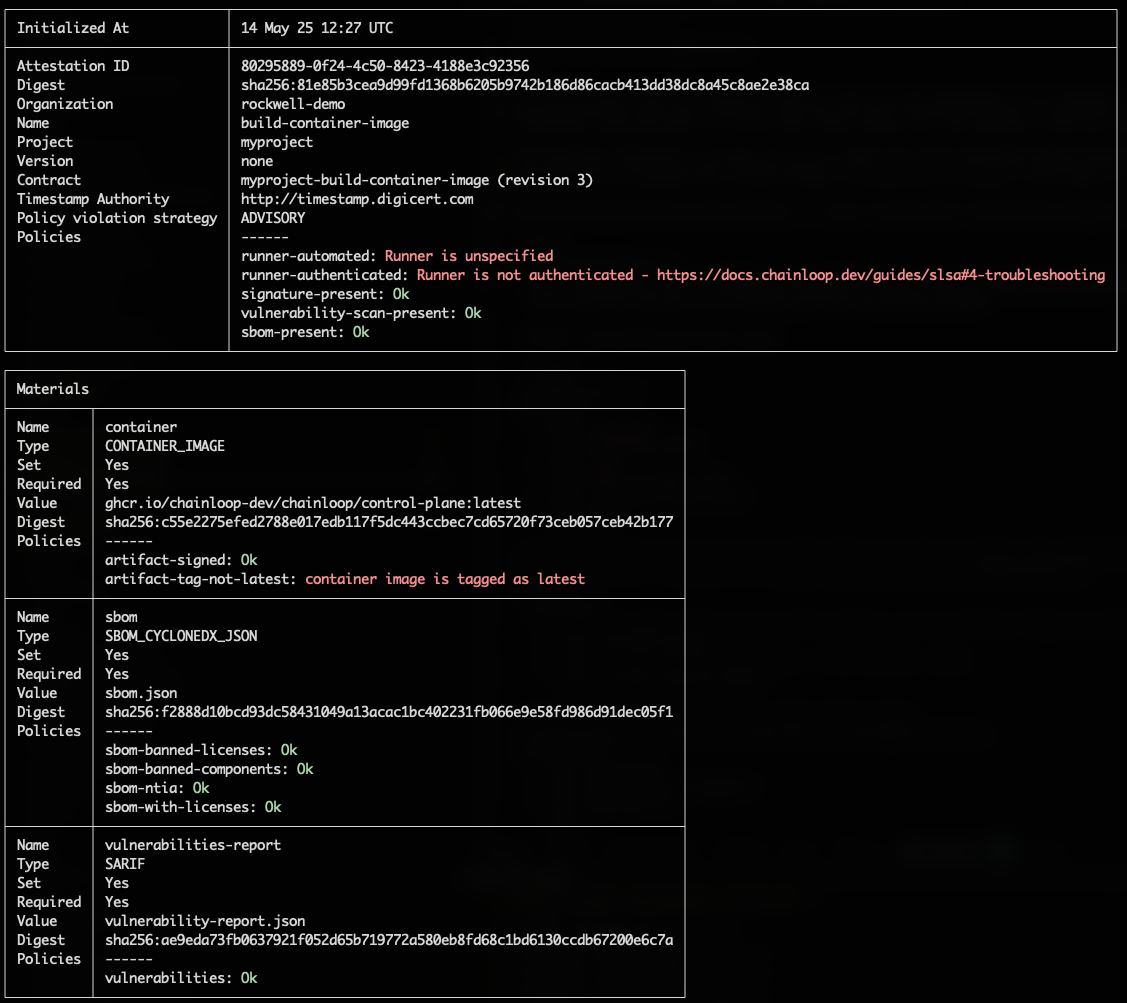
- the ones related to the build-environment, since we are running the attestation process locally.
- the one that checks the container image is not using the
latesttag.
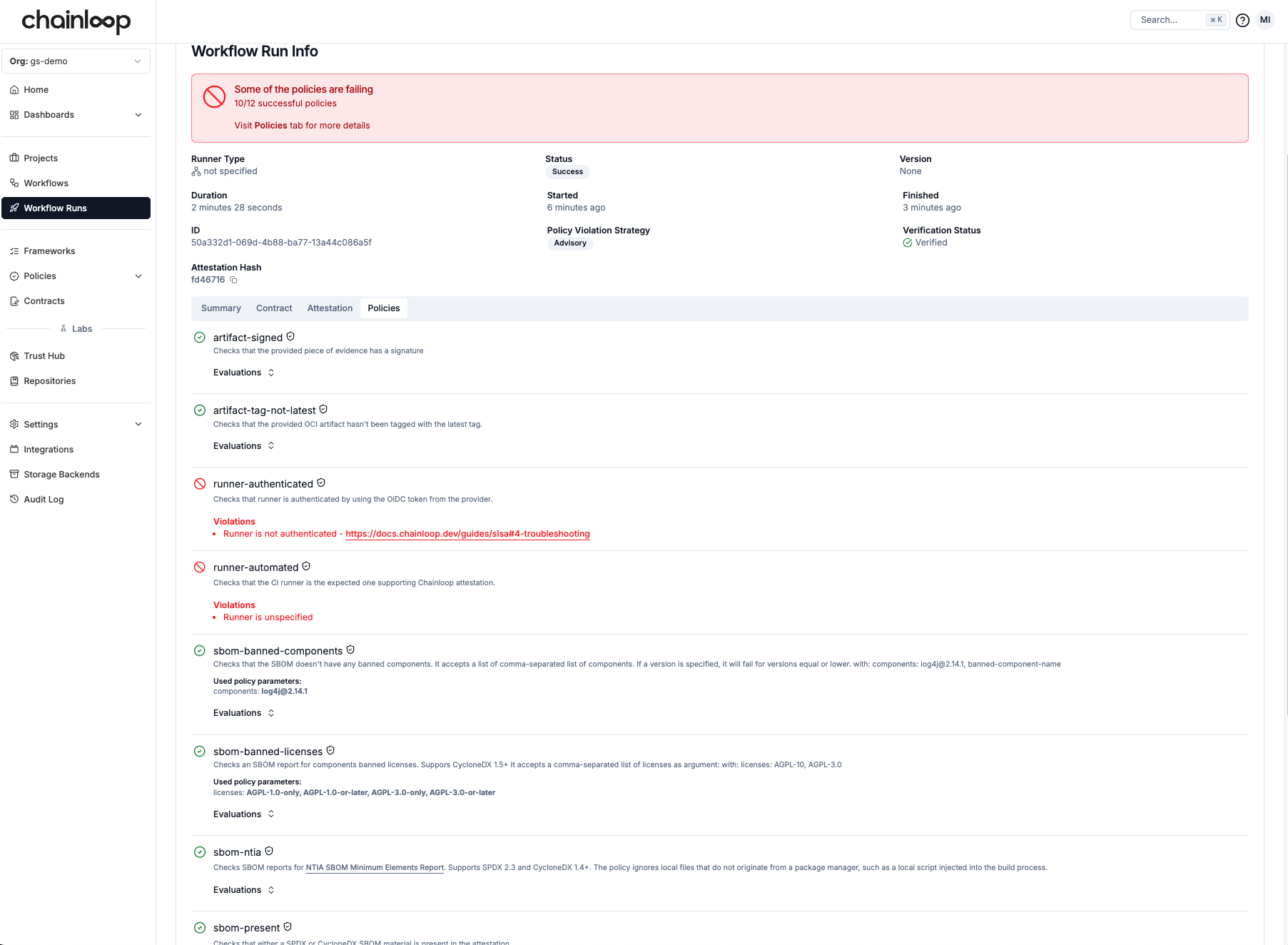
Inspecting policy evaluations
Now, the Chainloop platform gives us more insights into the status of the attestation. If we go to the workflow run view, besides the usual attestation and material information, we can now see the result of those policy evaluations.